 Overview
Overview
The Privacy & Security module is responsible for establishing secure system connections, including the implementation of an OTP-based authentication system. It supports both direct access and API interactions with the platform. Key features include password management, ticket-based authentication mechanisms, and the specification of permissible media file types for use by both customers and agents.
Learn more about specific topics, such as API Keys, SSO, 2FA, and more, in the articles within this section. For additional information about our product security, data privacy, and compliance, check our Trust Center.
Key Considerations:
- The security settings defined for the channel take precedence over those configured in the Privacy & Security module.
- OTP is valid for 10 minutes and allows up to 5 attempts. Upon successful verification, the editing window remains active for one hour.
- Editing of sensitive information is only granted to verified admins and agents with the required permissions.
Module Settings
General
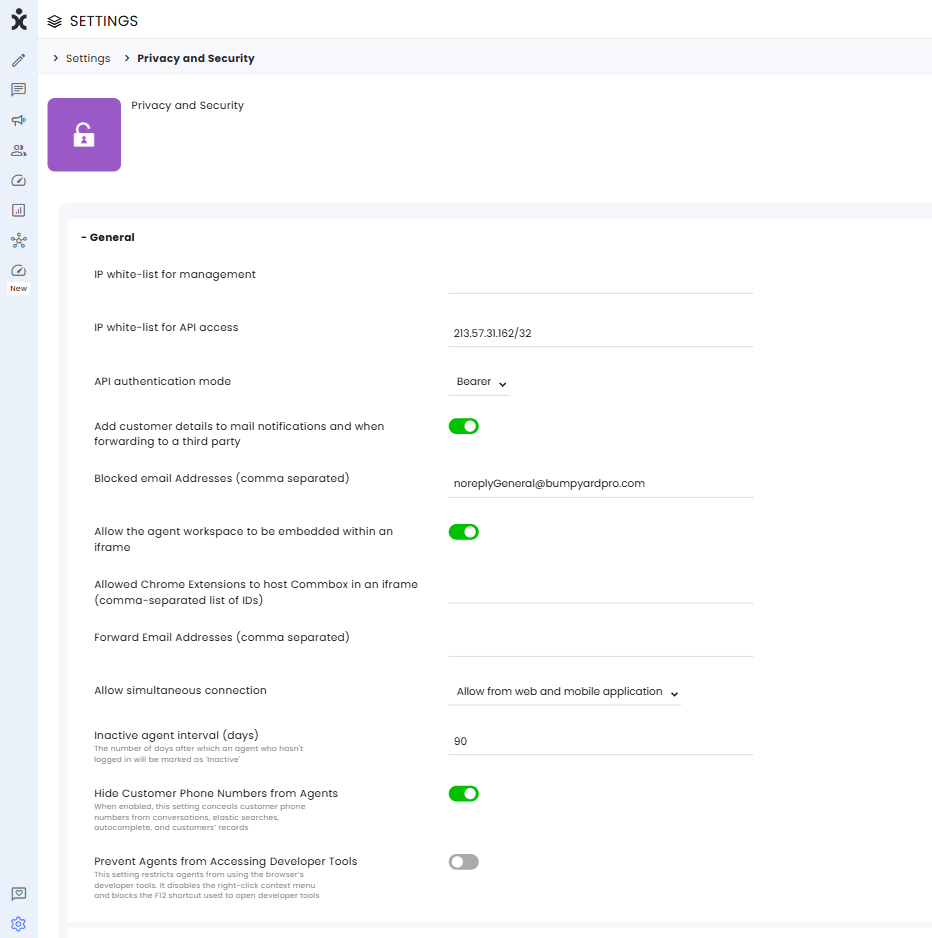
IP whitelist for management : This list specifies the IP addresses authorized to connect to the system. If no IP addresses are defined, the system will allow connections from any IP address.
When one or more IP addresses are specified (separated by commas), only those addresses will be permitted to connect. Exceptions to this rule may apply if overridden by settings in the 2FA module.
IP whitelist for API access : This setting defines the IP addresses permitted to send API requests to the system. If one or more IP addresses are listed, all other addresses will be blocked and will receive errors when attempting to make requests.
If no IP addresses are specified, all addresses will be authorized to send API requests to the system.
API Authentication mode : This setting is responsible for how you receive the Access Token in API conversations.
The API key is available in the API Key Module on the Settings page.
Add customer details to mail notifications and when forwarding to a third party : When activated, the customer's details will be included in email notifications and can be redirected to an external third party by clicking the three-dot icon next to the conversation ID.
Block email Addresses (comma separated) : Add the email addresses of the “do-not-reply” messages.
Allow the agent workspace to be embedded within an iFrame : Enables agents to work within the CRM with the CommBox system embedded in the screen.
Allowed Chrome Extensions to host CommBox in an iframe (comma-separated list of IDs): Add authorized Chrome extension IDs to the CSP allowlist, enabling those extensions to access CommBox content alongside existing iframe permissions.
Note: The Allow the agent workspace to be embedded within an iFrame toggle must be enabled in order to embed the iframe. In most cases, organizations do not experience security conflicts when embedding the CommBox iframe and can leave this configuration blank.
Forward Email Addresses (comma separated) : Addresses listed in this field define the external third parties authorized to receive data. If no addresses are specified, data can be transferred to any external party.
Allow simultaneous connection :
This setting controls user access to the platform:
- Do Not Limit: Users can open multiple web tabs and connect via the mobile app simultaneously.
- Allow from web only: Limits access to the web, blocking mobile connections.
- Allow from web and mobile application: Permits one web tab and one mobile app connection per user.
Inactive agent interval (days): Specifies the number of days of inactivity after which an agent who hasn’t logged in will be marked as 'Inactive'.
Hide customer Phone numbers from agents - When enabled, this setting conceals customer phone numbers from conversations, elastic searches, autocomplete, and customers’ records.
Prevent Agents from Accessing Developer Tools - This setting restricts agents from using the browser’s developer tools. It disables the right-click context menu and blocks the F12 shortcut used to open developer tools.
Note: This capability is designed to deter casual attempts to inspect the DOM or API calls. However, it does not provide complete protection, as advanced users may still bypass client-side restrictions.
Password management
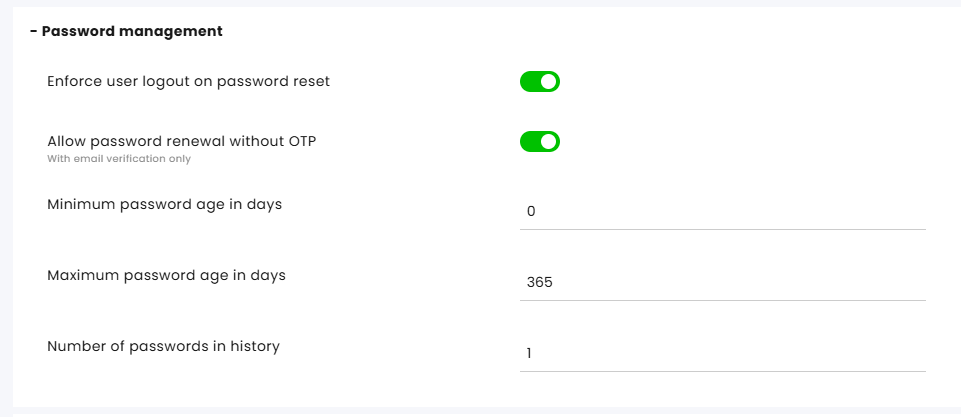
Enforce user logout on password reset: When a system administrator resets a user’s password, that user will be automatically logged out of all active sessions. Users receive a notification informing them that an administrator has reset their password and that they are being logged out.
Allow Password Renewal Without OTP: Enables password reset without requiring SMS verification.
Minimum Password Age (in days): Specifies the minimum period before a password can be reset. For example, if set to 5 days, the password can only be reset after 5 days from the date it was last changed.
Maximum Password Age (in days): Defines the maximum duration a password can remain unchanged. For instance, if set to 30 days, the system will require a password change every 30 days at the latest.
Number of Passwords in Password History: Determines the number of previously used passwords saved by the system that cannot be reused. For example, if set to 2, users cannot reuse any of their last three passwords when resetting a password.
Session management
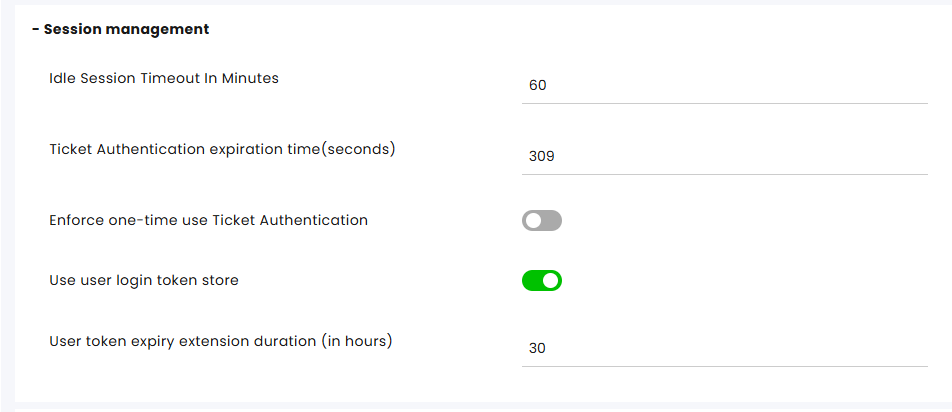
Idle Session Timeout (in minutes): Specifies the duration of user inactivity after which the system automatically logs the user out. To continue using the system, the user must log back in.
Ticket Authentication Expiration Time (in seconds): Relevant for chat-based channels only. This defines the time limit during which end customers can contact you via one of the enabled apps without logging in. This setting is particularly useful for organizations with customer-facing personal account pages, such as a "My Account" section on their website.
Enforce One-Time Use Ticket Authentication: When enabled, the system overrides API requests for Ticket Authentication tokens and issues tokens for single use only. This setting is off by default.
Click here to learn more about Ticket Authentication.
Use User Login Token Store: A CSRF (Cross-Site Request Forgery) cyber security mechanism that is toggled on by default and should always remain enabled.
User Token Expiry Extension Duration (in hours): Specifies the validity period for login tokens. Token expiry extensions are managed automatically by the system.
Media
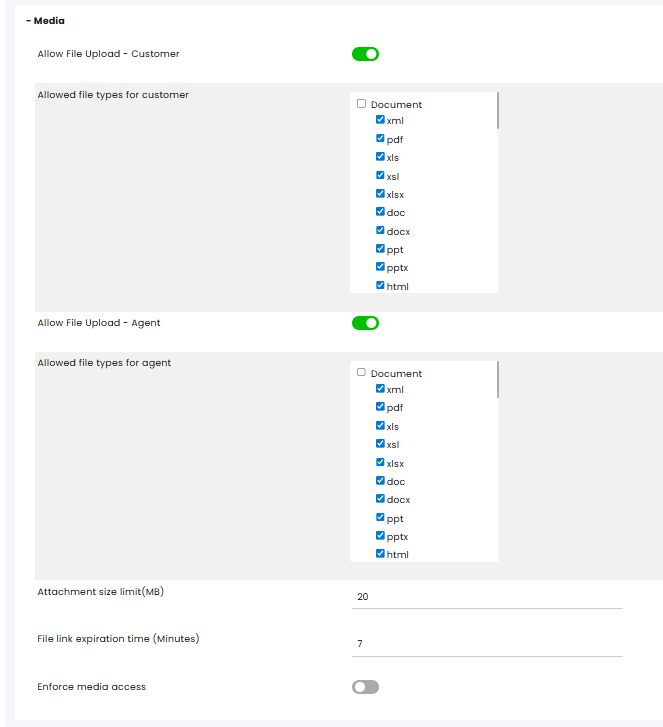
Allow Customer to Upload Files: Enables customers to send files to the system.
File Type Options for the Customer: Defines the types of files that customers are permitted to upload to the system.
Allow File Upload (Agent): Enables agents to send files to the system.
File Type Options for the Agent: Specifies the file types that agents are permitted to upload to the system.
Maximum File Size: Sets a limit on the file size for uploads, with a maximum of 30 MB.
Enforcing Media Access: Allows access to any media item in the system via a link. When enforcement of media access is enabled, the link can only be opened from a device that is connected to the system.
Notes:
- OPUS and OGG files can be downloaded in their original format but cannot be previewed or played directly in CommBox.
- For WhatsApp, only OGG files encoded with the OPUS codec are supported, with the following limitations: mono input only and a maximum file size of 16MB. Click here for more information.
Audit Trail Logs
Audit Trail Logs provide a detailed chronological record of the activities within the organization, which plays a critical role in security and compliance events.
Click here for the user guide.
Channel Settings
The Private & security settings defined for the channel take precedence over those configured in the Privacy & Security module. Below are some of the more unique features related to the different modules.
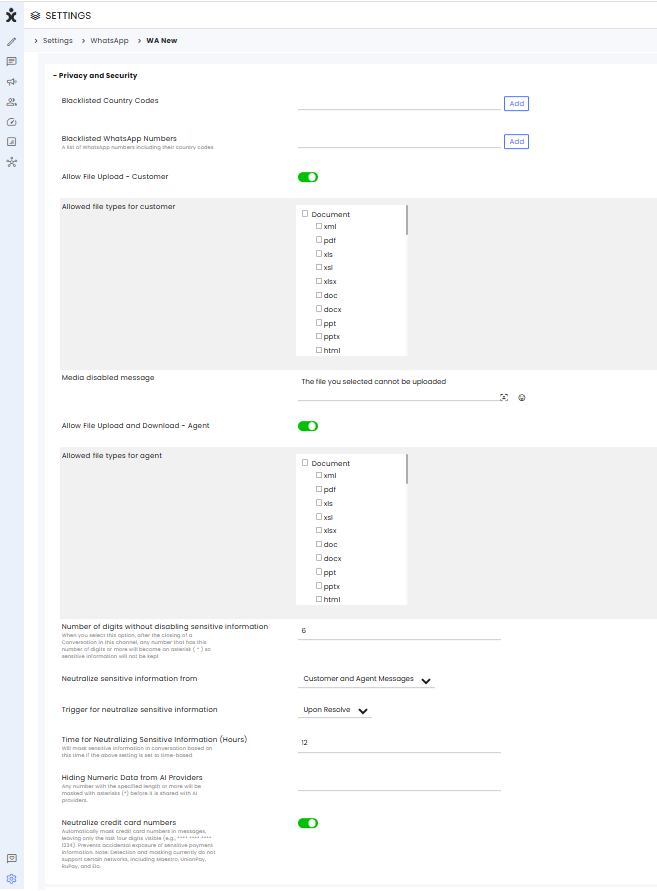
Blacklisting
Unique to WhatsApp channels, admins can blacklist phone numbers based on country code or specific WhatsApp numbers.
Redacting Sensitive Information
To protect sensitive information in customer-agent interactions, admins can enable automatic redaction. Sensitive data can be masked either when the conversation is resolved or after a predefined time interval (12-72 hours) from the message's creation.
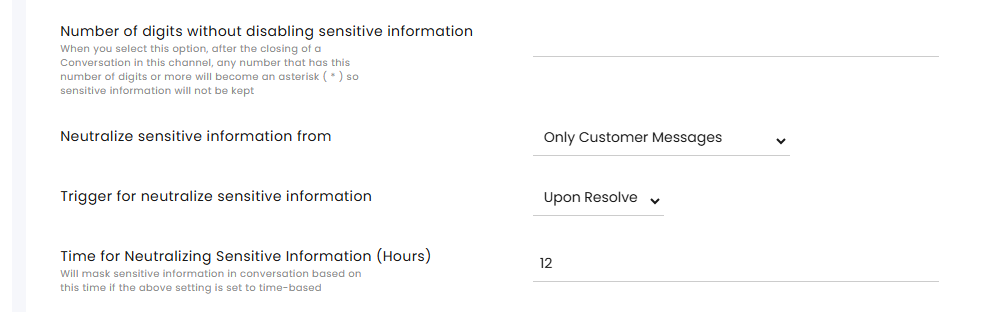
- Select the number of digits that will trigger the masking action. Numbers with that many digits or more will be masked with asterisks (*) to protect sensitive information.
- Select the type of messages that will be masked: Customer messages only or Agents and Customer messages.
- Select the trigger for the masking action
- Off - no automatic masking action
- Upon Resolve - Masking will automatically happen when the conversations are Resolved.
- Time-based – Masking will automatically happen X hours after creation.
- When selecting the Time-based option, select the number of hours from message creation that will pass before the masking takes place (12-72 hrs).
Applies to all direct messaging (DM) channels where customers send messages, including:
- Chat
- Instagram DM
- WhatsApp (WA)
- Telegram
- Facebook Messenger
- SMS
- Video Chat
- Voice Chat
Credit Card Numbers Auto Masking
To enhance security and protect customer information, enable the Neutralize Credit Card Numbers option in the channel settings. This feature automatically masks credit card numbers, displaying only the last four digits while replacing the rest with asterisks (*). Non-credit card numbers remain visible and unaffected.
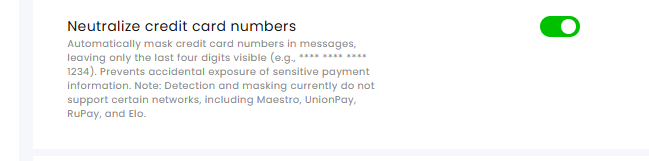
Note: This detection and masking functionality does not currently support Maestro, UnionPay, RuPay, or Elo card networks.
Hiding Numeric Data from AI Providers
For added security, admins can limit the number of digits visible to the AI engine. Enter the number of digits that will prevent the AI engine from seeing numbers with that many digits or higher.

Note that numbers will be block independently of usage, so for example, when selecting the number 4, exact addresses will not be identified as well (e.g., 1200 Ocean Parkway).
Chat Related Channel Settings
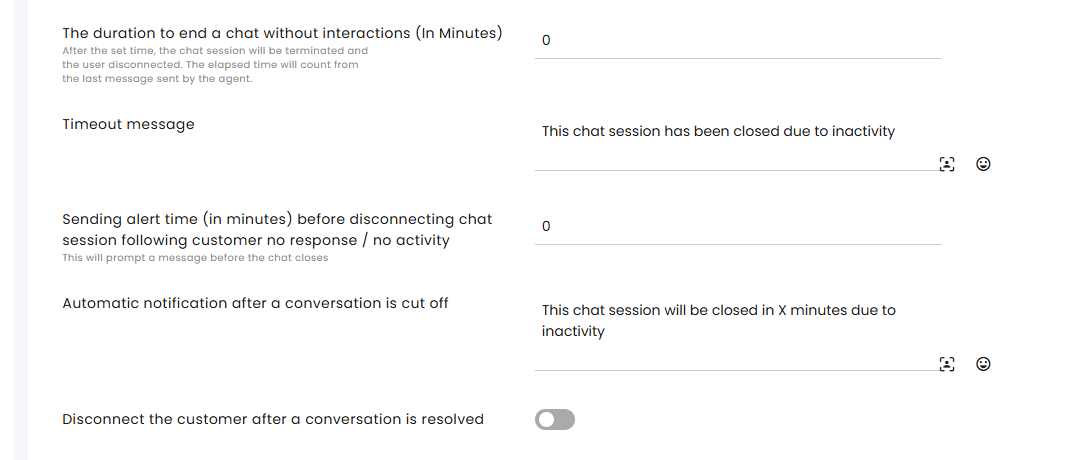
The duration to end a chat without interactions (In Minutes) – Enter the number of inactive minutes that will trigger the automatic disconnection of the chat session.
Timeout message – Enter the message that will be sent to the customer when the session is discontinued due to inactivity.
Sending alert time (in minutes) before disconnecting chat session following customer no response / no activity – Enter the number of inactive minutes, after which a warning will be sent to the user before the session is discontinued.
Automatic notification after a conversation is cut off – Enter the message that will be sent to the customer when the session is about to be discontinued due to inactivity.
Disconnect the customer after a conversation is resolved – Enable automatic disconnection at status change.